Exploiting apps replacing _init through shared libraries
Yes, an old topic, but this time, with a different and interesting approach. This time, Rh0 found a new attack vector, taking advantage of Glibc's shared library.
It reminds me the old LD_PRELOAD technique ;). Anyway, this time, everything is on dlopen(3), so, let's take a look into the man-page:
"The four functions dlopen(), dlsym(), dlclose(), dlerror() implement the interface to the dynamic linking loader... The function dlopen() loads the dynamic library file named by the null-terminated string filename and returns an opaque "handle" for the dynamic library."
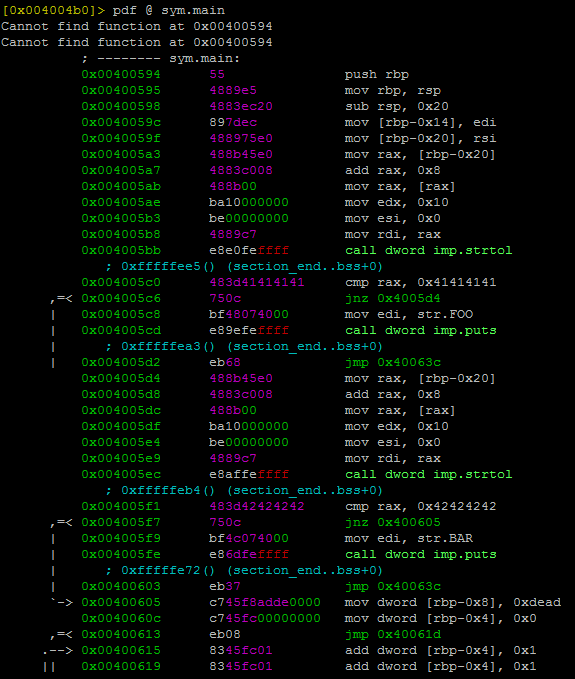
Independently the binary was compiled with RTLD_LAZY (Lazy Binding) or RTLD_NOW, the dynamic linker always execute the content of _init, which in a C programm it's defined by the function with the attribute __attribute__((constructor)) assigned.
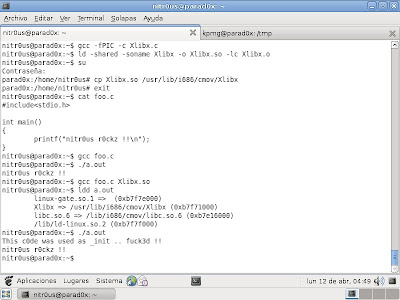
So, I tested this in my leasure time and the results are displayed in the next screensh0t.
ch33rz!
It reminds me the old LD_PRELOAD technique ;). Anyway, this time, everything is on dlopen(3), so, let's take a look into the man-page:
"The four functions dlopen(), dlsym(), dlclose(), dlerror() implement the interface to the dynamic linking loader... The function dlopen() loads the dynamic library file named by the null-terminated string filename and returns an opaque "handle" for the dynamic library."
Independently the binary was compiled with RTLD_LAZY (Lazy Binding) or RTLD_NOW, the dynamic linker always execute the content of _init, which in a C programm it's defined by the function with the attribute __attribute__((constructor)) assigned.
So, I tested this in my leasure time and the results are displayed in the next screensh0t.
ch33rz!

Comentarios
Publicar un comentario