SANS Toronto - I got the Flag in the CTF ! ;)
Well, I'd like to post my experience at SANS 560 CTF (Captuer The Flag), which was held on May 10th at the Intercontinental Toroton Centre in Toronto, Canada.
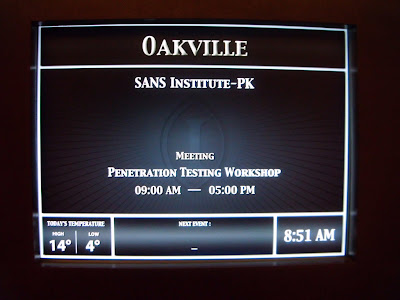
Everything started at 9 am and 4 specially configured & hardened servers and 2 routers were setup in order to break into them. Anyway, it was one of the most challenging CTF's I ever had, 'cause I showed up my COMPLETE NINJA SKILL-SET B-D !!.. yeahh baby !!
Well, the challenge was about to get a 4-times GPG encrypted file, by different people, and then, decrypt it in the inverse order it was encrypted. So, the challenge was to obtain the public and private keys from the 4 different users from the Windows and Linux b0xes.
Ready, set, go !!... Then, I started my ninjutsu h4ck1ng, and also, I had no time to eat, nor time to go to the restroom, I had only time to go for phree c0ffee while my GBs of RAM-resident rainbow tables were destroying some NTLM hashes and my source-c0de patch3d John the ripp3r was cracking others *UNIX accounts.
So, teh hard work was based on some of the f0llowing n1nj4 skillz:
Keep r0cking !! B-) !

Everything started at 9 am and 4 specially configured & hardened servers and 2 routers were setup in order to break into them. Anyway, it was one of the most challenging CTF's I ever had, 'cause I showed up my COMPLETE NINJA SKILL-SET B-D !!.. yeahh baby !!
Well, the challenge was about to get a 4-times GPG encrypted file, by different people, and then, decrypt it in the inverse order it was encrypted. So, the challenge was to obtain the public and private keys from the 4 different users from the Windows and Linux b0xes.
Ready, set, go !!... Then, I started my ninjutsu h4ck1ng, and also, I had no time to eat, nor time to go to the restroom, I had only time to go for phree c0ffee while my GBs of RAM-resident rainbow tables were destroying some NTLM hashes and my source-c0de patch3d John the ripp3r was cracking others *UNIX accounts.
So, teh hard work was based on some of the f0llowing n1nj4 skillz:
- MOSTLY TACTICAL EXPLOITATION (yes, use of the BRAIN)
- netcat hardc0re ninj4 hacking, using *NIX backpipes ($man mknod with the 'p' parameter for n00bz) in order to chain different b0xes/ports to bypass FW rules..
- Hardc0re packet analysis, specifically capturing traffic with tcpdump with very specific pcap filters and sending the output somewhere you can reach it through a wind0wz machine in order to analyze all the traffic so as to detect a specific pattern to continue the attack against other servers (LOT OF PEOPLE DIED HERE xDDD, n000bz)
- Very Rude ! UNIX commands !!! (not for newbies B-D !! like j00 !!!) and STDIN, STDOUT, STDERR deeeeeeeeeeeep knowledge
- Rem0te and privilege scalation Exploits' source code modification and compilation...
- iptables knowledge in order to append some SPECIFIC rule sets (no iptables -F allowed for kiddies xDDD)
- Using l33t techn1quez like passing-the-hash to SMB services to PWN other win b0xez !! ;) (yes n00b, I know it's the first time you read about it xDDD)
- d3crypting files using stolen public and private GPG keys (yes, I know, it was the easy part =D)
Keep r0cking !! B-) !
my respect
ResponderEliminar