IOActive Labs Research: A Short Tale About executable_stack in elf_read_implies_exec() in the Linux Kernel
by Alejandro Hernández @nitr0usmx
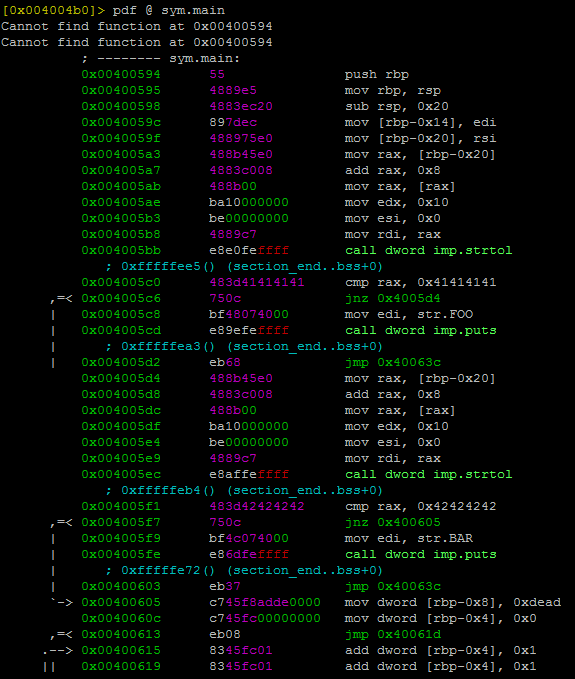
This is a short and basic analysis I did when I was uncertain about code execution in the data memory segment. Later on, I describe what’s happening in the kernel side as well as what seems to be a small logic bug....
READ THE WHOLE PAPER HERE:
IOActive Labs Research: A Short Tale About executable_stack in elf_read_implies_exec() in the Linux Kernel
...
Anyway, perhaps that’s the normal behavior of the Linux kernel for some compatibility issues or something else, but isn’t it weird that making the stack executable or deleting the PT_GNU_STACK header all the memory segments are loaded with execution permissions even when the PF_EXEC flag is not set?
This is a short and basic analysis I did when I was uncertain about code execution in the data memory segment. Later on, I describe what’s happening in the kernel side as well as what seems to be a small logic bug....
READ THE WHOLE PAPER HERE:
IOActive Labs Research: A Short Tale About executable_stack in elf_read_implies_exec() in the Linux Kernel
...
Anyway, perhaps that’s the normal behavior of the Linux kernel for some compatibility issues or something else, but isn’t it weird that making the stack executable or deleting the PT_GNU_STACK header all the memory segments are loaded with execution permissions even when the PF_EXEC flag is not set?
What do you think?
Comentarios
Publicar un comentario